Contrary to what one might think, security is a myth. There are no fully secure solutions. Just look at the past few years, with the attack on Sony’s infrastructure, to attack the Iranian uranium centrifuges or media conflict between Apple and the FBI, which brought to stardom Israeli company Cellebrite in said “impossible” unblocking iPhone.
in this way we will address more thoroughly the issue of security in applications for Android.

it all comes down to a matter of commitment, both in resources and in time, to achieve break and enter any system. Examples par excellence are the safes. To put it briefly, the evaluation of these is based on the time that a “thief” professional needs to break into using mechanical and electrical processes without destroying the contents. A safe class “TL-15″ must, according to the norm endure 15 minutes of torture, with mechanical instruments and / or electrical, before being opened.
Choosing a good security system
the secret in choosing a good security system in both the real world and the digital world is to find a solution that is more difficult to penetrate and raise the risk of be caught, so that our thief did not see an opportunity, but a source of annoyance. We need to show your impudence you will get expensive.
That said, now speaking in the digital world and more precisely in Android applications, there are simple steps you can take to make life difficult for the pirates. And what’s even an Android application? There is more than a compressed file, the ZIP format, with apk extension (Android Package), which is read by the Android installer, responsible for defining space, create folders and copy the files in the appropriate destinations and then run by the system . operating when requested by the user
Within an Android typical Package, we have the following structure:
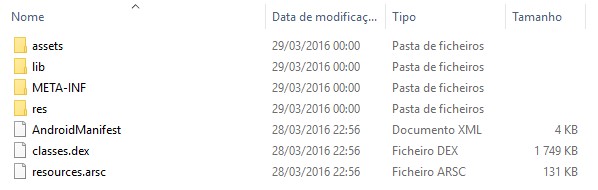
Illustration 1 – Structure of an APK file
assets folder contains all file attachments such as images, icons or help files. In META-INF directory are the files of the signatures contained in the apk and the res directory, we have the graphics, icons and splash, used by the Launcher Android.
the settings and the necessary privileges to run the application are recorded in AndroidManifest.xml, and the mapping of the graphics used in the code are in resources.arsc. Finally, and not least, we have the classes.dex (Dalvik Executable) with the compiled code.
This is where it becomes interesting. A native Android application will be compiled code in classes.dex and images, and other resources used, located in the assets folder.
One of the features of Android is not to use the classic Java virtual machine, but a new virtual machine called Dalvik, created from scratch, designed and optimized to increase the speed and reduce sizes. Not used the Java bytecode. Instead, DEX was added. For example, a Java application, class is compiled for each individual class file, while the DEX all classes are together in one file. Another advantage of DEX is the size, usually more than 50% lower than uncompressed JAR.
Despite these differences, you can convert the DEX in JAR. We have several freeware applications available for that purpose. The best known is the dex2jar, available on Sourceforge, and other repositories. We download, decompress the package and run the application, pointing to our apk
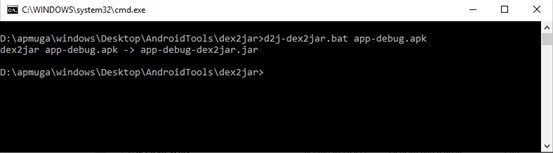
Illustration 2 – DEX conversion to JAR
decompress the JAR file, also in ZIP format, and use one of many decompilers available for JAVA class to convert the file. Personally I like to use the JD-GUI Java Decompiler, Emmanuel Dupuy
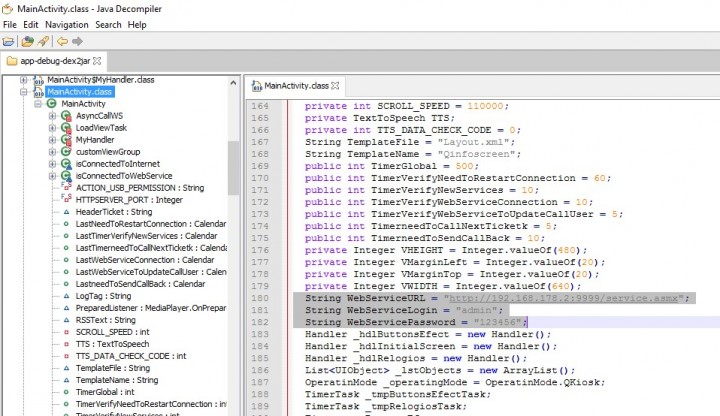
Illustration 3 – JD-GUI Java Result Decompiler
Taking a hybrid application, based on the PhoneGap, the process is very simpler. This will be your code, html and javascript, free text, distributed in assets folder, leaving the PhoneGap plugins in classes.dex.
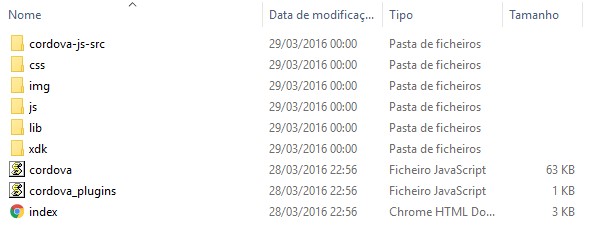
Illustration 4 – Structure of a PhoneGap application
With all this, we can change the code and reverse the process. Compiled, we created the JAR, we converted to DEX, with the help of d2j-jar2dex. We need to re-create the hash of each file, based on the jarsigner, and compress everything in a new apk file.
How to Get an apk? For those who have installed adb, we can connect to the device and directly pull the apk.
adb connect xxx.xxx.xxx.xxx:5555
adb shell pm list packages
adb pull /data/app/exemplo.app.pt.apk
for those who have hurry, we can use applications available GOOGLEPLAY like APKoptic or APK Extractor (Backup Apk) and save the file in sd card and then download our pc .
How to know the id of the apk you want to analyze? When browsing in GooglePlay, to the product presentation page, we read in the browser url, your id.
https://play.google.com/store/apps/details?id = exemplo.app.pt.apk
in other ecosystems, iOS, Blackberry and Windows, the process is similar, although the level of difficulty is greater. In fact Apple devotes a lot of energy security. Applications are digitally signed at the Apple Store to be installed on a specific device. The control is much higher, and this includes programmers. But there is always a but, to jailbreak an iPhone, lay on the ground this barrier.
Is it possible to protect our applications or have to accept fearlessly this? The answer it is neem. You can not have a full guarantee. However, it is possible to prevent. You can make the task of such herculean so do give any novice hacker.
First, the security must be thought from the beginning. We must know the defense mechanisms that our election platform offers and draw our application accordingly. You can not start coding and wait for the obfuscation of code do miracles. We must assume that our code will be seen. So obfuscate the code is essential. It does not solve the problem, but part of the solution. For native applications, Android Studio, just set up and activate the Proguard. For hybrid applications, we can use the Google Closure Compiler with the level of ADVANCED_OPTIMIZATIONS build.
Even obfuscated, we have another problem. Strings and configuration values, such as address access and encryption keys, are available to more prying eyes. The place is definitely not in the code. Should be out, ideally set in the installation, the “Internal Storage”.
“Internal Storage” is a space created by Android, exclusive of application access and are not accessible to other processes in activity, or the same user. Even so, a device “rooteado”, this is no guarantee of safety. You can corrupt the operating system and access to “Internal Storage”. Then we need to encrypt the data. Nowadays, systems chip (SoC) have a Trusted Execution Environment (TEE). It is with their differences of each implementation, each manufacturer of a virtual processor with the ability to create and manage private keys, totally inaccessible the rest of the ongoing processes. By the way this is usually module that manages keys used by wifi cards of the same SoC.
The use could not be simpler. We have created a key, which is stored internally and safe inside the chip.
try {
// existing certificate Validates. If you do not create …
string lv_strAlias = “Internal Storage Cert”;
if (keyStore.containsAlias (lv_strAlias)! ) {
Calendar lv_dtBegin Calendar.getInstance = ();
Calendar lv_dtEnd Calendar.getInstance = ();
lv_dtEnd.add (Calendar.YEAR, 1);
KeyPairGeneratorSpec lv_objSpec = new KeyPairGeneratorSpec.Builder (this)
.setAlias (lv_strAlias)
.setSubject (new X500Principal ( “CN = Test”))
.setSerialNumber (BigInteger.ONE)
.setStartDate (lv_dtBegin.getTime ())
.setEndDate (lv_dtEnd.getTime ())
.build ();
KeyPairGenerator lv_objGenerator KeyPairGenerator.getInstance = ( “RSA”, “AndroidKeyStore”);
lv_objGenerator.initialize (lv_objSpec);
keypair lv_objKeyPair lv_objGenerator.generateKeyPair = ();
}
} catch (Exception e) {
Log.e (TAG, Log.getStackTraceString (e));
}
we can create keys we need, for example, one for the Internal Storage, which encode all and guarantee that the data will only be used in this equipment . We may have another certificate for communication with the XPTO server, we provide the public key to the server.
String lv_strInitialText = “Example of information”;
String lv_strEncryptedText = “”;
try {
KeyStore.PrivateKeyEntry lv_objPrivateKeyEntry = (KeyStore.PrivateKeyEntry) keyStore.getEntry (lv_strAlias, null);
RSAPublicKey lv_objPublicKey = (RSAPublicKey) lv_objPrivateKeyEntry.getCertificate () getPublicKey ();.
Cipher lv_objInput = Cipher.getInstance ( “RSA / ECB / PKCS1Padding”, “AndroidOpenSSL”);
lv_objInput.init (Cipher .ENCRYPT_MODE, lv_objPublicKey);
ByteArrayOutputStream lv_objOutputStream ByteArrayOutputStream = new ();
CipherOutputStream lv_objCipherOutputStream = new CipherOutputStream (lv_objOutputStream, lv_objInput);
lv_objCipherOutputStream.write (lv_strInitialText.getBytes ( “UTF-8″));
lv_objCipherOutputStream.close ();
byte [] = lv_lstVals lv_objOutputStream.toByteArray ();
lv_strEncryptedText.setText (Base64.encodeToString (lv_lstVals, Base64.DEFAULT));
} catch (Exception e) {
Log.e (TAG, Log.getStackTraceString (e));
}
Committing one KeyStore is possible, but we enter another dimension in the security world. Each manufacturer will have its implementation, its defense mechanisms and their failures. From time to time arise from failure News A or B. We have to keep up to date and see their implications in our applications.
The use of keystore is a good solution, but with restrictions. For example, the keystore is available when the device is locked and requires user authentication by code or fingerprint – small detail we need to remember when designing a service. However, combining the various points that we have seen so far, we have a reasonable assurance that it will take much more than 15 minutes pirating.
No comments:
Post a Comment