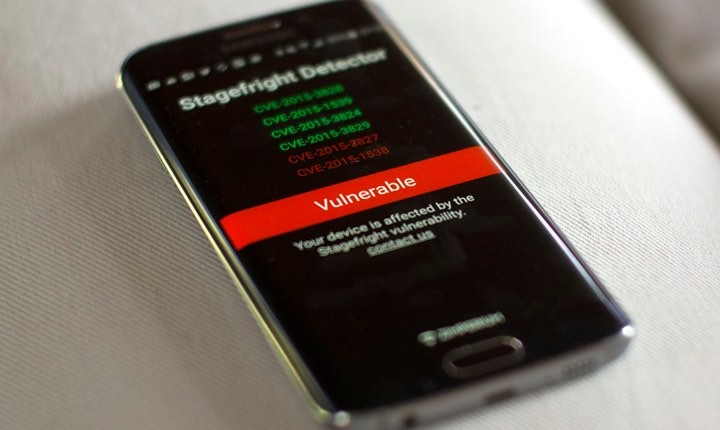
The discovery of Stagefright and simple way it is possible to attack almost all Android devices let the Internet and users aware of these devices.
The Google and manufacturers were quick to react to the problem, with the availability of a fix, but ultimately the solution can not solve anything and the problem still persists.
>
Everything seemed to indicate that the problem would be solved Stagefright simply, with Google and manufacturers to release security updates at a pace that was amazing and all the view that when it was necessary brands solve problematic situations of Android.
A few days after emerging the Stagefright Google problem could create a fix that would address this situation, and it passed immediately to manufacturers.
Taking advantage of this need, the brands and the Google pledged to launch monthly security update, which would deal with new situations, thus ensuring the Android better quality at this level.
With these updates to be released for now only for the Nexus, but scheduled very soon on manufacturers like Samsung or LG, now comes the news that after the Stagefright is not fully corrected and that can still be explored.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 | Fix When integer overflow handling MPEG4 tx3g atom When the sum of the 'size' and 'chunk_size' variables is larger than 2 ^ 32 , an integer overflow Occurs. Using the result value to allocate memory leads to an undersized buffer allocation and later the Potentially exploitable heap corruption condition. Ensure que integer overflow does not occur. Bug: 20923261 Change-Id: Id 050a36 b33196864bdd98b5ea24241f 95a0 b 5D1 f diff --git a / media / libstagefright / MPEG4Extractor.cpp b / media / libstagefright / MPEG4Extractor.cpp 8e47fda..ab1dade index 100 644 --- a / media / libstagefright / MPEG4Extractor.cpp + ++ b / media / libstagefright / MPEG4Extractor.cpp @@-1,897.6 +1897.10@@ size = 0 ; } + if ( SIZE_MAX - chunk_size & lt; = size ) { + return ERROR_MALFORMED; + } + uint8_t * buffer = new ( std :: nothrow ) uint8_t [ size + chunk_size ] ; if ( == NULL buffer ) { return ERROR_MALFORMED; |
Apparently the 4 lines of code that Google added to Android in the form of a patch to solve one of Stagefright failures are not enough and, according to researchers from Exodus Intelligence, this failure may still be used to achieve execute malicious code into the Android.
To test that the fault was still present researchers from Exodus sent an mp4 file via MMS and then managed to exploit it. It was not clear if they could accomplish was the execution of code and disconnecting Android.
Google has been confronted with this situation and quickly released a new patch to fix, it is expected that definitively the problem. Also this new correction was sent to manufacturers, which must shortly launch it for their equipment.
The arrival of this fix to Google equipments happen with the release of the September security fixes. Until then users will be exposed to Stagefright.
OS remaining manufacturers have to apply a similar measure to launch the correction, it is expected for the next month on arrival in the equipment.
Something important that the Exodus was revealed that would hardly have also been the ones to detect that the correction had problems and that probably there will be abuse of the problem, and the users must keep the same measures that were recommended to mitigate the problem until a solution Final arises.
No comments:
Post a Comment