Unlock Codes (Unlock Pattern) Android is an iconic feature that Google introduced in 2008 and which is widely used by users.
But is this really safe functionality these days? A recent study has revealed who the users tend to frequently use the same patterns that can be compared to passwords like “123456″ or “p @ $ $ w0rd”.

Today a smartphone is like a diary of our lives. We keep photos, videos, chat with friends, or a lot of personal information that does not like to see so disclosed. The initial unlock code is one of the security mechanisms to protect our device but the truth is that it’s so ineffective … really you because users use mostly the same.
An unlock code may have Numbers at least 4 and at most 9, providing a maximum of 389 112 combinations. As passwords, the complexity increase as you increase the size of the word.
This is the number of combinations taking into account the number of size chosen to unlock codes.
| Size | Combination |
| 4 | 1,624 |
| 5 | 7,152 |
| 6 | 26.016 |
| 7 | 72.912 |
| 8 | 140.704 |
| 9 | 140.704 |
Mars Loge the Norwegian University of Science and Technology, recently analyzed more than 4,000 ALPs (Android lock Patterns), as part of his thesis and was created three imaginary APLs for apps: Shopping , smartphone and Photo . The findings were immediate:. Most users would use APLs with only 4 digits for most apps
As you can see by the graph below, the clusters with 8 digits are rare and there is hardly a reason to do so.
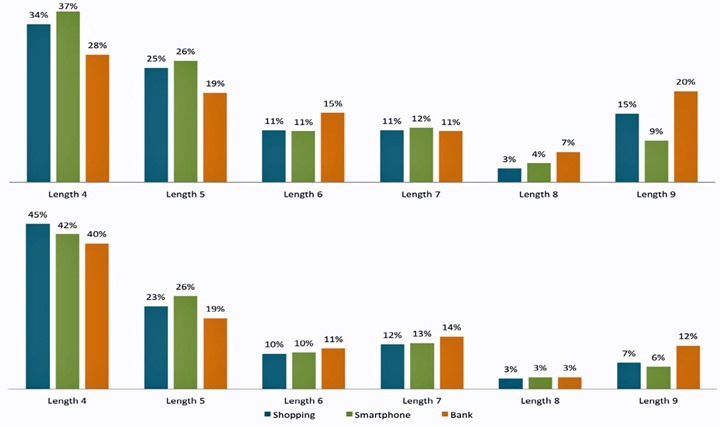
the first line charts correspond to the results of men and the second line to women
The realization of this thesis also served to conclude that the users use weak APLs (very popular) that can be compared to passwords like “123456″ or “ p @ $ $ w0rd” (used by many). To emphasize even qu and about 10% of users use an APL corresponding to the first letter of the name of your child.
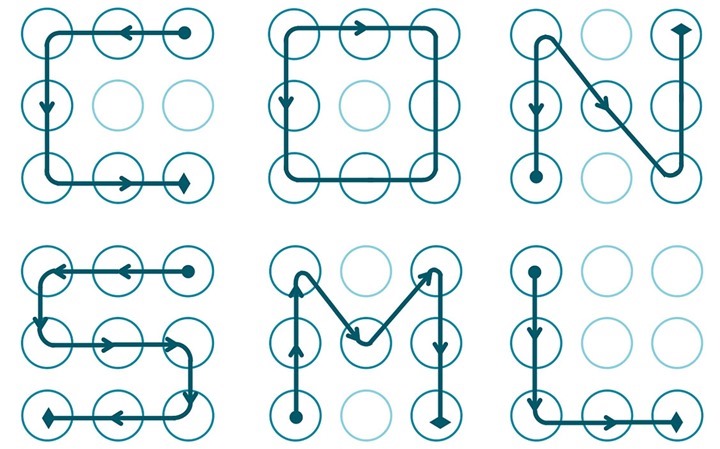
As the APL an Android security mechanism, it is very important to define a cluster complex so that it is not easily discovered by someone malicious. had already thought of that?
Via Arstechnica
No comments:
Post a Comment