10% of the apps they want to access the list of contacts and 4% to the user’s calendar. More intrusive apps are Google’s own
. <-. Post-summary ->
 In the mobile apps economy, is it less consumer software than consumed by it. This according to the security firm Zscaler who analyzed the surprisingly intrusive permissions demanded by many popular applications in the App Store Google before allowing your download. [The company conducted another study for the ecosystem of iOS apps.]
In the mobile apps economy, is it less consumer software than consumed by it. This according to the security firm Zscaler who analyzed the surprisingly intrusive permissions demanded by many popular applications in the App Store Google before allowing your download. [The company conducted another study for the ecosystem of iOS apps.]
Of these, 28% were also able to have access to SMS -. risk because it can be abused to spy mobile authentication used by banks and other online services such as Gmail, PayPal and Twitter.
In view of Zscaler, riskier permissions coveted by legitimate applications cover SMS, GPS and access to calls phone the ability to read the information on personal accounts, the device being used and access to the contact list.
The company stresses that even experienced users give permission to applications for access this data type, why not do it often means that the application can not be installed. This calls into question the whole model based on permission used not only by Android, Google, but for all mobile platforms.
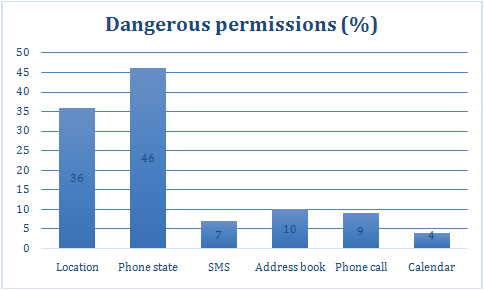
Analyzing other permissions, Zscaler also found that 36% access the user’s location, 46% to your device (IMEI and SIM card information), 10% to the contact list and 4% even check the calendar.There are legitimate reasons for an application want to access all or parts of it, being the most intrusive of Google’s own applications. But many other intrusive ask permission, as part of a business model built to offer a free application within which it operates a network of advertising which is intended to gather as much information as possible to better target your message.
The permissions for the list of contacts are often part of a model in which an application is promoted in address book of the user. Sometimes this happens with the consent of the same but not always the case – the complaints about the “kidnapping” of the list of addresses have become widespread in some messaging applications in Android, so that Google was forced to change its terms and conditions for developers earlier this year.
No comments:
Post a Comment